| SUPPLEMENT No. 49December 19, 2020
Who Determines
What Constitutes a Threat to National Security
It Is Up
To Canadians, Not the Police, to Decide What Constitutes a Threat to
"National Security" - Anna
Di Carlo -   
• Canada's
Foreign-Inspired "Threat Assessments" - Pauline Easton -
• Threat
Assessments Driven by Business Interests - Nick Lin -
• Fearmongering About Canada's Supply
Chain •
Indian
Disinformation Operation •
Second U.S. Judge Blocks
President's Attempt to Ban
China-Based Social Media App
Who
Determines What Constitutes a Threat to National Security -
Anna Di Carlo - Threat assessments issued by
Canada's intelligence agencies are replete with messages which target
speech and association deemed to pose threats to national security. The
Marxist-Leninist Party of Canada has gone on record to oppose the use
of the threat of foreign interference in elections and/or "our
democratic institutions" and/or our "way of life," to justify the
violation of Canadians' right to speech and association. By any modern
definition fit to be called democratic, the people have the right to
oppose state interference in their right to speak and associate freely.
An anti-China motion currently before the House of Commons and
current "assessments" by the intelligence agencies of "threats to
national security" show that the approach of the Liberal Government and
of the Conservative Party, which considers itself the government in
waiting, is to authorize police powers to monitor and surveil political
speech and activities in search of "foreign interference." We are to
believe that opposing "foreign interference" will sort out the vicious
inter-imperialist rivalry over markets, sources of cheap raw materials
and labour, and zones for the export of capital and influence in
Canada's favour. Will giving the U.S. imperialists' war machine and
their aggressive NATO military alliance absolute control over 5G and 6G
technology sort out the problems facing humanity or, for that matter,
the fundamental problems that ail our utterly unrepresentative
electoral system? The answer is No!  According to the
Liberal government and the cartel parties with seats in the House of
Commons, the only problem facing our electoral system and democratic
institutions is interference by hostile foreign states and hostile
non-state actors. This is considered a matter of national security and,
presumably, national unity as well. The problem, identified by
Canadians time and time again, that our electoral system -- called a
representative democracy -- and our "democratic institutions" do not
represent the views of the majority of the population, is not acted on.
The fact remains that this electoral system is designed to keep the
people disempowered and to perpetuate a ruling caste which pays the
rich. According to the
Liberal government and the cartel parties with seats in the House of
Commons, the only problem facing our electoral system and democratic
institutions is interference by hostile foreign states and hostile
non-state actors. This is considered a matter of national security and,
presumably, national unity as well. The problem, identified by
Canadians time and time again, that our electoral system -- called a
representative democracy -- and our "democratic institutions" do not
represent the views of the majority of the population, is not acted on.
The fact remains that this electoral system is designed to keep the
people disempowered and to perpetuate a ruling caste which pays the
rich.
The preoccupations of the intelligence
agencies and security forces dominate the discourse so as to hide the
fact that the state has been put in the service of the U.S. imperialist
rivalry with China and that the U.S. war economy covets the great
advances China has made in putting artificial intelligence (AI) to
practical use. This deepens the crisis in which the electoral and
political processes are mired and does nothing to create confidence
that they can achieve a mandate resulting from the political
participation of Canadians. Police monitoring of
political discourse in a search for malicious foreign actors is not
going to solve the problem of the "fake news" these foreign actors are
said to generate. Implicating the civilian population and political
parties in cooperating in their spying activities is not going to end
the discourse and disinformation which is carried out on a massive
scale through the communications networks which have already come into
being and those that are coming into being today. Far
from it, to foster the belief that "hostile foreign states" and
non-state actors are the problem, the intelligence agencies themselves
churn out "fake news" and conduct a large number of disruptive
activities through their communications networks. The recent example of
what India has been up to worldwide, including in Canada, is a case in
point. The already revealed and as yet unrevealed activities of the
intelligence agencies into which Canada has been integrated, which do
the exact same things, is another. The claim of the
security agencies that their surveillance of political discourse is not
aimed at "lawful advocacy and dissent," is silly talk. We
are told that "lawful advocacy and dissent is a healthy part of
democracy," as opposed to "clandestine or deceptive foreign
interference." But the criteria for deciding who and what can be
investigated and targeted for surveillance operations and what will be
considered "lawful" is all kept hidden in the name of national
security! Investigations and surveillance are to find "threats which
may, on reasonable grounds, be suspected of posing a threat to the
security of Canada," we are told. In other words,
political expression and speech will be targeted in surveillance
operations to safeguard national security. The claim is that it is not
by upholding rights that we defend national security, but by their
violation. One of the threats to national security
the intelligence agencies have cited in the past is the "discrediting
of liberal-democratic institutions in order to advance alternative
governance models." What is wrong with advancing alternative governance
models? By what definition can it be said that "advancing alternative
governance models" is a threat to Canada's security? Who determines the
definition? By what process?  Surely, the very
definition of democracy gives the people the right to decide what
governance models suit their needs. How can that right be taken away
from people in the name of national security, using the justification
that it is the police, not the people, who are responsible for the
preservation of the institutions of democracy? If the security agencies
are concerned about who poses the threat to our democratic
institutions, we suggest they turn their eyes to the very ruling party
government and cartel parties whose everyday actions are de facto changing
the model of democratic governance which came out of rebellion against
rule by decree. It is their self-serving shenanigans which have brought
the democratic institutions, cartel parties, government and House of
Commons into disrepute. Surely, the very
definition of democracy gives the people the right to decide what
governance models suit their needs. How can that right be taken away
from people in the name of national security, using the justification
that it is the police, not the people, who are responsible for the
preservation of the institutions of democracy? If the security agencies
are concerned about who poses the threat to our democratic
institutions, we suggest they turn their eyes to the very ruling party
government and cartel parties whose everyday actions are de facto changing
the model of democratic governance which came out of rebellion against
rule by decree. It is their self-serving shenanigans which have brought
the democratic institutions, cartel parties, government and House of
Commons into disrepute.
It is not acceptable, by
any definition or any norms save those of a police state, that, based
on intelligence reports and discussions with "elected officials," CSIS
can be permitted to take "reasonable and proportionate measures" to
interfere with the right to speech and association. Such police
activity is indefensible in a country which calls itself democratic and
claims that it is the people, not the police agencies of the state,
which determine what views are in the interest of Canada's progress and
advancement, and which views are not. To accuse other countries of
tyranny and dictatorial rule, neither of which are defined in a manner
that means something rational in today's conditions, does not hide that
the shoe fits their own foot.

-
Pauline Easton - Communications Security
Establishment Canada's Centre for Cyber Security issued a "National
Cyber Threat Assessment 2020" on November 16. To evaluate its
assessment it is important to know the criteria it uses. However,
neither are these criteria openly explained, nor are they up for
discussion. On the contrary, one has to discern the criteria for
oneself and seriously think about what criteria would serve the peoples
when discussing national security. Without establishing the reference
points which serve the peoples and society, the "key judgments" of the
Centre for Cyber Security remain unchallenged. Not only that, they are
used by the government, by the cartel parties with seats in the House
of Commons, and by state agencies across the board to pass laws,
criminalize individuals and collectives, and fund war production.
 The Executive
Summary of the CSE's Centre for Cyber Security's report provides what
it calls seven "Key Judgments." One of its claims is that "threat
actors will almost certainly continue attempting to steal intellectual
property related to combatting COVID-19 to support their own domestic
public health responses or to profit from its illegal reproduction by
their own firms." The Executive
Summary of the CSE's Centre for Cyber Security's report provides what
it calls seven "Key Judgments." One of its claims is that "threat
actors will almost certainly continue attempting to steal intellectual
property related to combatting COVID-19 to support their own domestic
public health responses or to profit from its illegal reproduction by
their own firms."
Why China, Russia and Iran need
to "steal intellectual property related to combatting COVID-19" when
they have minds of their own second to none in the world is a real
stretch. It illustrates the high degree of paranoia the intelligence
agencies are intent on promoting. Creating hysteria against the target
countries is the same method used in the recent period when hysteria
against Muslims and Islamophobia were promoted and raised to fever
pitch, all the while accusing others of xenophobia. Every Muslim was
considered either a terrorist or a potential terrorist and entire
countries were invaded and subjected to bombs, assassinations, torture,
drone warfare and every conceivable crime against human beings.
Evidence of how the ruling circles are creating hysteria to attack
China and infiltrate terrorist groups there is the justifications given
that such actions defend the Uighurs who are Muslims and
presumably not acceptable to the Chinese government. Meanwhile, pogroms
organized by the ruling government in India against the Muslim
population there were met with silence. Similar arguments are used to
justify infiltrating Tibet and organizing anti-China instability
there. All of it is a reincarnation of
state-organized disinformation to keep the polity diverted, divided and
overwhelmed so that it does not establish an agenda which serves its
interests and those of humankind. These hysterical threat assessments
appear to be designed to make it impossible for the people to address
what the rulers themselves are up to. This includes deciding what
constitutes a cyber threat, a crime and cyber warfare, that justifies
aggression. The assessments are based on an outlook designed to tear
Canadians apart based on whether they support or oppose whatever the
security agencies say poses a danger to society. The
modus operandi
is well known. The climate of hysteria is despicable for its harmful
anti-social consequences due to the added stress and anxiety and
criminalization of people who are dehumanized and categorized as
"criminal," or "traitor," or "spy," labels which presumably mean they
deserve whatever they have coming to them. It is
also quite well understood in many circles that reports that raise the
spectre of threats and dangers posed by foreign actors serve to lobby
for increased funding for security agencies and all their tools and
toys. Massive spending is devoted to cyber security which is linked
with the defence industry and war production.  One method used,
which is less well understood, is how the security agencies try to
embroil the people in diversions. One is a demand against the
involvement of social media companies in cyber spying, which is a just
demand. However, the security agencies manipulate the anti-war movement
into waging campaigns which are then used to cover up the fact
that the big social media companies are funded by the war department of
the United States from the time they emerge on the scene. One method used,
which is less well understood, is how the security agencies try to
embroil the people in diversions. One is a demand against the
involvement of social media companies in cyber spying, which is a just
demand. However, the security agencies manipulate the anti-war movement
into waging campaigns which are then used to cover up the fact
that the big social media companies are funded by the war department of
the United States from the time they emerge on the scene.
The
striving of the war industry to control artificial intelligence is
driving the narrow private interests involved into a frenzy and,
consequently, entire societies that are subject to their threat
assessments are also made unstable. Obscene sums of money are handed
over to the war industry while members of the polity are criminalized
and anxiety over potential threats becomes the rallying cry for
national unity.
Scientific discoveries
belong to humanity. The new developments in 5G networks and the
scientific advancements made by Chinese scientists in quantum
encryption are new forms of mass communications being brought forward
by the social productive forces. Such developments are not the property
of anyone. This is the greatest significance of these new developments
in the experiments in ultra-secure communications which are so
important for the functioning of any high speed network. No single
entity, whether a nation or corporation can control or monopolize it
because it is based on the law of physics which can be applied
universally. This is also the case for the fruits of artificial
intelligence which tread where science has never even been before.
Science and scientific discoveries belong to humanity. The demand of
the peoples of the world is to use the products of the technical
scientific revolution for the enhancement of the human species.
 The younger
generation is born to this technology and to a world in which
scientific discoveries are revolutionizing all hitherto comprehension
of the universe. This generation also comprises the majority of those
called cyber actors and cyber criminals. This kind of fearmongering
will only go so far to justify spending on the war industry and its
destructive capacity. The younger generations will develop the
capabilities needed to bring a world of peace, justice and democracy
into being, as they are already doing in many ways. The younger
generation is born to this technology and to a world in which
scientific discoveries are revolutionizing all hitherto comprehension
of the universe. This generation also comprises the majority of those
called cyber actors and cyber criminals. This kind of fearmongering
will only go so far to justify spending on the war industry and its
destructive capacity. The younger generations will develop the
capabilities needed to bring a world of peace, justice and democracy
into being, as they are already doing in many ways.
Against
this, the one-sided self-serving view of the rulers of what the
ensemble of social relations reveals is clear in each one of the "key
judgments" of the Canadian Centre for Cyber Security. Never
once do the authors consider that removing the current anti-democratic
system of rule will go a long way to solving the problems societies
face. The only concern of those who have usurped power by force is to
imbue the entire world with their own profit-motive, in the misguided
belief that this will make the peoples of the world hand them riches
without question. As the rulers continue to dream
in Technicolor, the peoples of the world continue to lay the claims on
society for what belongs to them by virtue of being human. They
continue to strive for a society which will define rights on that basis.

- Nick
Lin - Covert state intelligence agencies tied to
the U.S. imperialist war machine as part of the "Five Eyes" global
espionage network recently issued their annual reports and "threat
assessments." The countries which belong to the "Five Eyes" are the
U.S., Canada, the UK, Australia and New Zealand. Private cyber security
firm the Kaspersky Lab, said to be "Russia-based," also recently issued
an assessment. What are called threats by the U.S.
imperialists and their allies are an indication of which countries will
be targeted for interference and aggression, including cyber warfare.
Such calculations are of interest to the anti-war movement and the
movement to defend the rights of all, so they can draw warranted
conclusions and not lose their bearings. It is important not to become
embroiled in the U.S.-led warmongering by getting sucked into the
scenarios created by the intelligence agencies to justify their latest
assessments of what constitutes a foreign or domestic threat.
 Strikingly absent
from all of these threat assessments are the threats to
privacy and political rights of the people of
those countries by their own governments.
Since the exposure of wide-ranging illegal surveillance by the National
Security Agency of U.S. citizens by whistleblower Edward Snowden in
2013, attacks on the privacy and political rights of the
people of the U.S. and of the other Five Eyes
countries have not been curtailed. They have
become institutionalized and even broader. Strikingly absent
from all of these threat assessments are the threats to
privacy and political rights of the people of
those countries by their own governments.
Since the exposure of wide-ranging illegal surveillance by the National
Security Agency of U.S. citizens by whistleblower Edward Snowden in
2013, attacks on the privacy and political rights of the
people of the U.S. and of the other Five Eyes
countries have not been curtailed. They have
become institutionalized and even broader.
One
of the major changes in U.S. legislation since 2013 has been to have
Internet Service Providers (ISPs) divulge metadata concerning their
clients, instituting what is called an obligation to provide a
"back-door" access to metadata. Such metadata can include
personal information, histories, etc. and highly sensitive material.
For their part, ISPs had been campaigning
against illegal intrusions by the state agencies and asking for
protection from state agency intimidation.
Part
of the raison
d'être of the Five Eyes is to spy on
each other's people to get
around the laws of their own countries. Since Canada, for
example, cannot legally spy on its own people, the spying is done by
the U.S. and the result is then "shared." Meanwhile, measures are being
taken to change the laws in each country to permit spying and
recriminations in the name of high ideals. The
threat assessments also have in common that they do not address the
well-documented practice of interfering in the political affairs of
other countries by U.S., Israeli, French, British and other
agencies through cyberattacks and other technical
manipulations. There are double standards
too when it comes to "foreign interference." For example, when the U.S.
openly interfered in the 2019 federal election in Canada through major
media gossip stories, an investigation of this as foreign interference
was not considered. For Your
Information
Canadian Centre for Cyber
Security's "Key Judgments" The Centre for Cyber
Security's "Key Judgments" are: "- The number of
cyber threat actors is rising, and they are becoming more
sophisticated. The commercial sale of cyber tools coupled with a global
pool of talent has resulted in more threat actors and more
sophisticated threat activity. Illegal online markets for cyber tools
and services have also allowed cybercriminals to conduct more complex
and sophisticated campaigns. "- Cybercrime
continues to be the cyber threat that is most likely to affect
Canadians and Canadian organizations. We assess that, almost certainly,
over the next two years, Canadians and Canadian organizations will
continue to face online fraud and attempts to steal personal,
financial, and corporate information. "- We judge
that ransomware directed against Canada will almost certainly continue
to target large enterprises and critical infrastructure providers.
These entities cannot tolerate sustained disruptions and are willing to
pay up to millions of dollars to quickly restore their operations. Many
Canadian victims will likely continue to give in to ransom demands due
to the severe costs of losing business and rebuilding their networks
and the potentially destructive consequences of refusing payment.
"- While cybercrime is the most likely threat, the
state-sponsored programs of China, Russia, Iran, and North Korea pose
the greatest strategic threats to Canada. State-sponsored cyber
activity is generally the most sophisticated threat to Canadians and
Canadian organizations. "- State-sponsored actors
are very likely attempting to develop cyber capabilities to disrupt
Canadian critical infrastructure, such as the supply of electricity, to
further their goals. We judge that it is very unlikely, however, that
cyber threat actors will intentionally seek to disrupt Canadian
critical infrastructure and cause major damage or loss of life in the
absence of international hostilities. Nevertheless, cyber threat actors
may target critical Canadian organizations to collect information,
pre-position for future activities, or as a form of intimidation.
"- State-sponsored actors will almost certainly continue to
conduct commercial espionage against Canadian businesses, academia, and
governments to steal Canadian intellectual property and proprietary
information. We assess that these threat actors will almost certainly
continue attempting to steal intellectual property related to
combatting COVID-19 to support their own domestic public health
responses or to profit from its illegal reproduction by their own
firms. The threat of cyber espionage is almost certainly higher for
Canadian organizations that operate abroad or work directly with
foreign state-owned enterprises. "- Online foreign
influence campaigns are almost certainly ongoing and not limited to key
political events like elections. Online foreign influence activities
are a new normal, and adversaries seek to influence domestic events as
well as impact international discourse related to current events. We
assess that, relative to some other countries, Canadians are
lower-priority targets for online foreign influence activity. However,
Canada's media ecosystem is closely intertwined with that of the United
States and other allies, which means that when their populations are
targeted, Canadians become exposed to online influence as a type of
collateral damage." U.S. Homeland Threat Assessment
The U.S. Department of Homeland Security (DHS) issued its
26-page Homeland Threat Assessment in October. It identifies seven
general categories of threats in the assessment's table of
contents. The following quotes from the report give an idea of what
the categories refer to.
- Cyber: "We are concerned
with the intents, capabilities, and actions of nation-states such as
China, Russia, Iran, and North Korea. Nation-state targeting of our
assets seeks to disrupt the infrastructure that keeps the American
economy moving forward and poses a threat to national security. On top
of the threats to critical infrastructure, cybercriminals also target
our networks to steal information, hold organizations hostage, and harm
American companies for their own gain." - Foreign
Influence Activity: "Threats to our election have been
another rapidly evolving issue. Nation-states like China, Russia, and
Iran will try to use cyber capabilities or foreign influence to
compromise or disrupt infrastructure related to the 2020 U.S.
Presidential election, aggravate social and racial tensions, undermine
trust in U.S. authorities, and criticize our elected officials. Perhaps
most alarming is that our adversaries are seeking to sway the
preferences and perceptions of U.S. voters using influence operations."
- Economic Security: "DHS is specifically
concerned with the direct and indirect threat posed to the Homeland by
the People's Republic of China (PRC). The Chinese Communist Party
(CCP)-led PRC is challenging America's place as the world's global and
economic leader. Threats emanating from China include damaging the U.S.
economy through intellectual property theft, production and
distribution of counterfeit goods, and unfair trade practices. DHS has
a mandate to mitigate these threats [...] with a clear-eyed view that
China is a long-term strategic competitor to the U.S." -
Terrorism: The
DHS presents its concerns about terrorism as two-fold, one aspect being
domestic violent extremism. It says its programs are
"threat agnostic," meaning DHS will decide across a broad
spectrum of "left," "right" and religious views, who and what is a
threat. They claim to be "particularly
concerned about white supremacist violent extremists who have been
exceptionally lethal in their abhorrent, targeted attacks in recent
years."
The other aspect
is to target the people's resistance movement, referring to it as the
"exploitation of lawful and protected speech and protests" and
"anti-government, anti-authority and anarchist violent extremism."
- Transnational Criminal Organization (TCOs):
The DHS says that these groups "continue to profit at the expense of
Americans. Mexican cartels and other TCOs will continue to smuggle hard
narcotics like fentanyl, heroin, and methamphetamine into our
communities, contributing to an alarming level of overdoses in the
United States. " - Illegal Immigration:
The DHS claims that "illegal and mass migration to the United States
[...] during a pandemic [...] poses a more specific threat to the
migrants, the communities they transit, to U.S. border communities, and
to our officers and agents who encounter migrants when they enter the
United States." - Natural Disasters:
The DHS cites here the threat posed by events like storms, wildfires as
well as the COVID-19 pandemic. Kaspersky Lab's
Advanced Threat Predictions for 2021 Kaspersky
Lab is a global cyber security company founded in 1997 with
headquarters in Russia. It issued its Advanced Threat Predictions for
2021 on November 16. A Kaspersky press release highlights the following
areas of concern from those it deems "advanced persistent threats"
(APTs): "- APT threat actors will buy initial
network access from cybercriminals. One of the key, and potentially
most dangerous, trends that Kaspersky researchers anticipate is the
change in threat actors' approach to the execution of attacks. Last
year, targeted ransomware attacks reached a new level through the use
of generic malware as a means to get an initial foothold in targeted
networks. Connections between these attacks and well-established
underground networks such as Genesis, which typically trade in stolen
credentials, were observed. Kaspersky researchers believe that APT
actors will start using the same method to compromise their targets.
[...] "- More countries using legal indictments as
part of their cyber strategy. Kaspersky's previous predictions of
'naming and shaming' of APT attacks carried out by hostile parties has
come true, and more organizations will follow suit. Exposing toolsets
of APT groups carried out at the governmental level will drive more
states to do the same, thereby hurting actors' activities and
developments by burning the existing toolsets of their opponents in an
effort to retaliate. "- More Silicon Valley
companies will take action against zero-day brokers. Following
scandalous cases in which zero-day vulnerabilities [i.e., security
flaws unknown to the software vendor on release date] in popular apps
were exploited for espionage on a variety of different targets, more
Silicon Valley corporations are likely to take a stance against
zero-day brokers in an effort to protect their customers and reputation.
"- Increased targeting of network appliances. With remote
work, organizational security has become a priority, and more interest
in exploiting network appliances such as VPN [virtual private network]
gateways will emerge. Harvesting credentials to access corporate VPNs
via 'vishing' remote workers may also appear. "-
Demanding money with menace. Ransomware gangs have become more targeted
in their attacks and have more often threatened to release stolen data.
Following the success of these strategies, the groups will use the
money they have extorted to invest significant funds into new advanced
toolsets with budgets comparable to that of some state-sponsored APT
groups. These changes in strategy may also lead to the consolidation of
the ransomware ecosystem. "- More disruption will
result from direct, orchestrated attacks designed to affect critical
infrastructure or cause collateral damage, as our lives have become
even more dependent on technology with a much wider attack surface than
ever before. "- The emergence of 5G
vulnerabilities. As adoption of this technology increases, and more
devices become dependent on the connectivity it provides, attackers
will have a greater incentive to look for vulnerabilities that they can
exploit. "- Attackers will continue to exploit the
COVID-19 pandemic. While it did not prompt changes in tactics,
techniques and procedures of the threat actors, the virus has become a
persistent topic of interest. As the pandemic will continue into 2021,
threat actors will not stop exploiting this topic to gain a foothold in
target systems." 
Prior to doses of a COVID-19 vaccine
being shipped across the country, the Canadian Security Intelligence
Service (CSIS) held a briefing for companies involved in the vaccine
supply chain. News reports on the CSIS briefing report predictions
of threats to Canada's supply chain by "malicious foreign
actors" who would exploit "vulnerabilities" of companies which form
part of the supply chain and their workers. "CSIS
observes persistent and sophisticated state-sponsored threat activity,
including harm to individual Canadian companies, as well as the
mounting toll on Canada's vital assets and knowledge-based economy,"
said a spokesperson for the agency. "As a result, CSIS is working
closely with government partners to ensure that as many Canadian
businesses and different levels of government as possible are aware of
the threat environment and that they have the information they need to
implement pre-emptive security measures." When
asked to specify which countries, the spokesperson referred to a July
briefing that CSIS gave to the Canadian Chamber of Commerce that
highlighted China and Russia as countries actively involved in
commercial espionage. A December 17 item from CBC
News cites various self-described "intelligence analysts" who take
their cue from CSIS's fearmongering to run wild with their own spectres
of possible "security threats."  One such analyst
suggests that the vaccine supply chain is "perhaps" a target because
Canada's adversaries would benefit from Canada not having access to
vaccines or not having a fully vaccinated population, or to undermine
confidence in the distribution system. She goes on to concoct that a
militant terrorist faction of those opposed to vaccines could seek to
disrupt their distribution. She concludes saying that if state security
agencies and the police are briefing those in the supply chain, then
there must be threat. This despite the many well-known examples of
fearmongering, black ops and state-organized terrorist activity by the
police and security agencies, to undermine and criminalize the people's
movement and organizations. One such analyst
suggests that the vaccine supply chain is "perhaps" a target because
Canada's adversaries would benefit from Canada not having access to
vaccines or not having a fully vaccinated population, or to undermine
confidence in the distribution system. She goes on to concoct that a
militant terrorist faction of those opposed to vaccines could seek to
disrupt their distribution. She concludes saying that if state security
agencies and the police are briefing those in the supply chain, then
there must be threat. This despite the many well-known examples of
fearmongering, black ops and state-organized terrorist activity by the
police and security agencies, to undermine and criminalize the people's
movement and organizations.
Former CSIS director
Ward Elcock is quoted as saying that organized crime is a threat. "If
you're a criminal organization, you can make money out of anything.
People make money off of cigarettes. They make money off of drugs. This
is no different than any other commodity." Of
course, the new vaccines are unstable and difficult to transport,
requiring specialized refrigeration infrastructure that is not readily
available. What purpose is served by a country's security establishment
sowing doubt about a modern society's ability to transport vaccines
safely, except for that security establishment to have increased funds
and deployment? One
participant in the briefing noted that the supply chain is very "data
rich" which makes it a target. A spokesperson for the Communications
Security Establishment (CSE) said, "CSE and its Canadian Centre for
Cyber Security continue to work with our domestic and international
partners to support the Government of Canada's response to the COVID-19
pandemic, including vaccine research and distribution. It is always
important to note that we continue to monitor for cyber threats through
our foreign intelligence mandate. We are working with our Canadian
security and intelligence partners, including the Department of
National Defence and the Canadian Armed Forces, to address foreign and
cyber threats facing Canada." Major-General
Dany Fortin, the military commander leading vaccination logistics at
the Public Health Agency of Canada, stated that "the underlying issue
that you're raising here is that we need to ensure that some
information is not divulged, for obvious reasons. So when it comes to
the exact routing [of vaccine shipments], we prefer not to disclose the
routing, the exact location or transfer points in the cold chain to
protect the integrity of the ... supply chain." All
of it indicates that those claiming to be responsible or knowledgeable
about "security threats" to Canada and its vaccine supply chain are
part of an outlook based on the premise that all countries must submit
to U.S. domination, and those that do not constitute a threat to
security. They seek to take advantage of people's high anxiety about
COVID-19 to justify increased powers for the state security agencies,
instead of uniting their thinking in actions which defend rights. In
the name of defending Canada against "malicious foreign
actors," Canadians are to rely on malicious foreign actors (e.g., the
U.S. imperialists, NATO, etc.), because agencies in the service of
those very malicious foreign actors say they can be trusted. It makes
no sense. 
A European Union (EU) non-profit group
called EU DisinfoLab, whose mission is to research disinformation
campaigns, has said it unearthed a 15-year-long Indian disinformation
campaign of massive proportions. DisinfoLab says that the campaign is
an influence operation "targeting international institutions and
serving Indian interests." The DisinfoLab Report is entitled "Indian
Chronicles: deep dive into a 15-year operation targeting the EU and UN
to serve Indian interests." The forward to the report says: 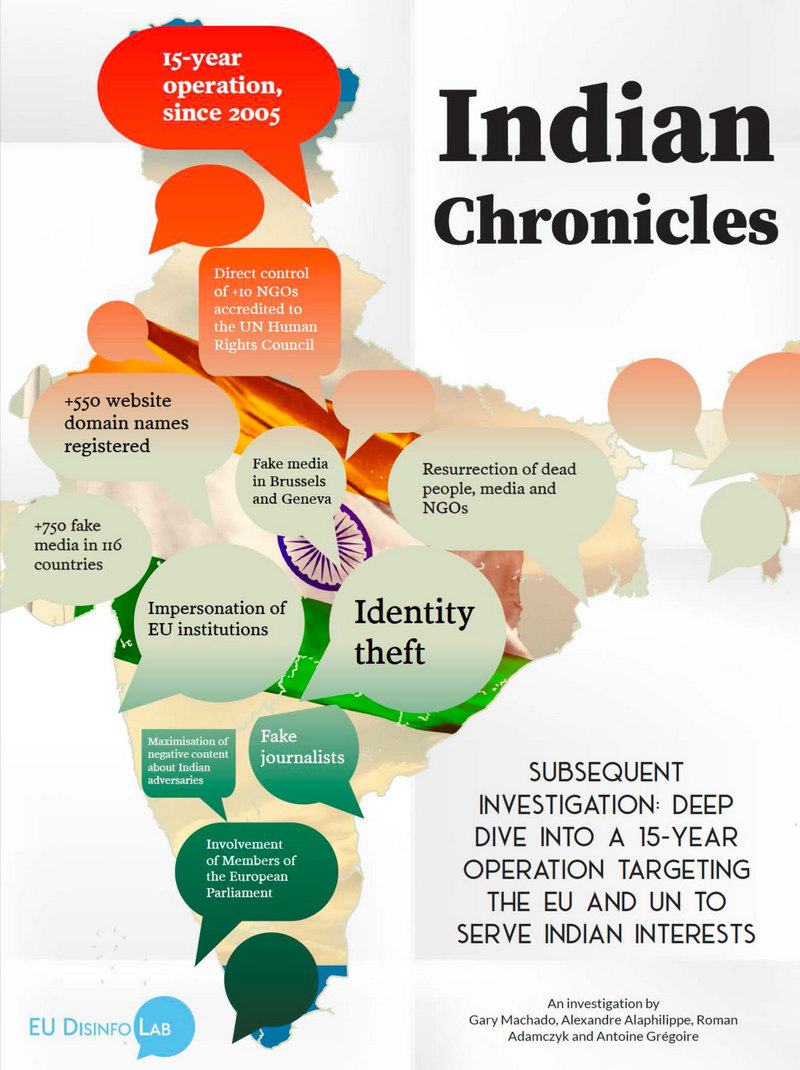 "'Indian
Chronicles' -- the name we gave to this operation -- resurrected dead
media, dead think-tanks and NGOs, as well as dead people. The actors
behind this operation highjacked the names of others, tried to
impersonate regular media and press agencies such as the EU Observer,
the Economist
and Voice of America, used the letterhead of the European Parliament,
registered websites under avatars with fake phone numbers, provided
fake addresses to the United Nations, created publishing companies to
print books of the think-tanks they owned. They organized supposedly
multi-stakeholder events where -- in essence -- everyone speaking was
tied to 'Indian Chronicles.' They misappropriated the picture of a
former UK Government Minister and BBC Director on Facebook, registered
the names of deceased persons to attend events five years after their
death, invented dozens of journalist identities. They used layers of
fake media that would quote and republish one another. They used
politicians who genuinely wanted to defend women or minority rights to
ultimately serve geopolitical interests and gave a platform to
far-right politicians when convergent objectives could be reached." "'Indian
Chronicles' -- the name we gave to this operation -- resurrected dead
media, dead think-tanks and NGOs, as well as dead people. The actors
behind this operation highjacked the names of others, tried to
impersonate regular media and press agencies such as the EU Observer,
the Economist
and Voice of America, used the letterhead of the European Parliament,
registered websites under avatars with fake phone numbers, provided
fake addresses to the United Nations, created publishing companies to
print books of the think-tanks they owned. They organized supposedly
multi-stakeholder events where -- in essence -- everyone speaking was
tied to 'Indian Chronicles.' They misappropriated the picture of a
former UK Government Minister and BBC Director on Facebook, registered
the names of deceased persons to attend events five years after their
death, invented dozens of journalist identities. They used layers of
fake media that would quote and republish one another. They used
politicians who genuinely wanted to defend women or minority rights to
ultimately serve geopolitical interests and gave a platform to
far-right politicians when convergent objectives could be reached."
The online publication The Wire reported
on December 10: "In 2019, EU DisinfoLab had
published a study that claimed to have uncovered an Indian influence
network covering '265 fake local news sites in more than 65 countries.'
"That study began as a probe into possible Russian
disinformation when articles published on Russia Today were republished
on a website, 'EP Today', which led the investigators to the network of
sites and NGOs, largely linked to the New Delhi-based Srivastava Group.
"This business firm was apparently the main backer of the
Delhi-based 'think tank,' International Institute of Non-Aligned
Studies (IINS) that had sponsored a group of right-wing members of
European Parliament (MEPs) to visit Kashmir in October 2019 -- the
first time any politicians (including Indian ones) were allowed to
visit the former state after it was placed in lockdown following the
scrapping of Article 370 [of the Indian Constitution] in August that
year. "Following up on its earlier study, the group
now says it has found evidence of a 15-year-old influence operation by
Srivastava group. "In the latest investigation
report -- 'Indian Chronicles,' released on Wednesday [December 9] --
the EU DisinfoLab claims to have identified over 10 NGOs accredited to
the United Nations Human Rights Council, which are apparently being
managed by the Srivastava Group. Most of these seem to have been
genuine NGOs which went into decline and whose identity has been
'hijacked,' as per the authors of the report. "For
example, in May 1938, the Canners International Permanent Committee was
founded to promote the 'consumption of canned food' and ceased to exist
in 2007. However, the domain name of the organization was registered on
January 10, 2016, 'the same day as the registration of other accredited
NGOs domain names, and it is hosted on the IP address with several
other Srivastava-owned websites.' "Accredited to
UNHRC, the organization has been making 'pro-Indian and anti-Pakistan'
oral interventions. 'The core theme of the original NGO -- 'canned
foods' -- was totally diverted to undermine Pakistan at the Human
Rights Council,' said the report. "Another
UN-accredited NGO to have a presence on the servers used by the
Srivastava Group, the report said, is the Commission to Study the
Organization of Peace (CSOP). "This organization
had been inactive from the late 1970s, before it was revived in 2005.
'Shockingly, we discovered that the organization had not only been
revived. Its former Chairman and 'grandfather of international law in
the U.S.,' Louis B. Sohn, who passed away in 2006, seemingly attended a
UN Human Rights Council meeting in 2007 and participated in an event
organized by 'Friends of Gilgit-Baltistan' in Washington, DC in 2011,'
the report says. "These groups were organizing side
events in the European parliament or UN offices, which were used to
bring in MEPs 'using causes such as minorities rights and women's
rights as an entry point.' Further, the report
claims that the 'actors' behind the operations registered over 550
domain names of NGOs, think-tanks, media, European Parliament informal
groups, religious and Imam organizations, obscure publishing companies
and eight public personalities. "EU DisinfoLab
claims to have found a new fake media -- 'EU Chronicle' -- which is
largely a platform for MEPs to sign pro-India articles. 'In less than 6
months of existence, already 11 MEPs, most of them already involved
with EP Today, have written or endorsed op-eds at a remarkably high
pace for EU Chronicle.' "These op-eds in EU
Chronicle were then repackaged by news agency ANI. 'Without Times
of Geneva and 4 News Agency which stopped their activities
following our previous investigation, ANI remains the only press agency
to extensively cover the activities of dubious NGOs in Geneva.'
"This media coverage, the report observed, was primarily
targeted at Indian nationals 'with an extensive coverage of these
barely known 'media', MEPs and 'NGOs' in Europe.' "Summarising
their findings, EU DisinfoLab said that their investigation details
'activities of a fake zombie-NGO and that of a fake specialized media
can then be repackaged, distorted and amplified by malicious actors to
influence or disinform globally, using loopholes in international
institutions and online search engines.' "The
researchers clarified that they were aware that the findings of the
report would be used by vested interests, in a reference to Pakistani
authorities. 'Let us bear in mind that it is not because one side uses
dodgy influence campaigns that the other side does not -- and a simple
Google search will lead you to read about inauthentic behaviours
supporting Pakistani interests,' they add." "This
report, they noted, was not a judgment about the situation of human
rights in Pakistan or undermine the credibility of minority movements.
"Asserting that there is no such thing as 'good
disinformation,' the authors claimed the 'report simply shines a light
on how Indian stakeholders have used these struggles to serve their own
interests.' "While the report did not point any
specific fingers at Indian intelligence agencies, it noted that there
were 'several elements that suggest the possible involvement of other
stakeholders' in the influence operations. These elements were
identified in the report as the close relationship between ANI and the
Indian government, a Srivastava group firm's alleged involvement in
offering information warfare services only to Indian agencies and
apparent threats made against a speaker at UN by a Srivastava group
member, followed by interrogation by Indian security agencies."
For the full report, click
here.

On December 8, Judge Carl Nichols of the U.S. District Court in
Washington, DC, ruled that the U.S. Commerce Department "likely
overstepped" its use of presidential emergency powers "and acted in an
arbitrary and capricious manner by failing to consider obvious
alternatives" regarding President Donald Trump's attempt to ban TikTok,
a social media app used to share short user-created videos.[1]
TikTok's Chinese parent company ByteDance filed suit against the ban on
September 18, arguing that the ban violated free speech and due process
rights. ByteDance proposed that TikTok's U.S.
operations be taken over by U.S. companies. The Trump administration
tentatively agreed in September that software giant Oracle and Walmart
invest in TikTok, in which Oracle would manage user data. This deal was
to have been finalized on December 6. The U.S. Treasury Department,
which oversees the agency reviewing this arrangement, said that the
agency "is engaging with ByteDance to complete the divestment and other
steps necessary to resolve the national security risks arising from the
transaction." Previously, a ruling from Judge
Nichols had temporarily blocked the presidential ban on September 27.
Then, U.S. District Judge Wendy Beetlestone, of the Eastern District of
Pennsylvania, ruled against the ban on October 30 in a suit filed by
three TikTok users against the presidential ban, who said it interfered
with their free speech. ByteDance reports 100
million TikTok users in the U.S. and 700 million worldwide. The Trump
administration says that TikTok is a security threat, claiming that the
Chinese government could use it to spy on users personal data. Trump
signed an executive order on August 6 which sought to ban TikTok
transactions in the U.S. by September 20 unless its Chinese parent
company ByteDance sold off its U.S. operations. This was followed by
another order on August 14 giving ByteDance 90 days to sell or spin off
TikTok's U.S. operations. The developments in the
TikTok case take place in the context of U.S. imperialists' attempts to
isolate China through fearmongering and anti-communist rhetoric, in
which escalating sanctions and trade wars threaten to break out into
open military aggression. There is no evidence to back up the Trump
administration's accusations against TikTok, while the U.S. government
is notorious for its long-established practice of cyber espionage or
cyber warfare on its own people and those of other countries.
This is a situation in which the ruling circles in Canada have
fully embroiled the country in anti-China intrigues in subservience to
U.S. imperialist interests. This includes the RCMP's arrest of Huawei
executive Meng Wanzhou, acting on a U.S. extradition request. Also
notable is the execrable use of Halifax as the venue for the Halifax
Security Conference, which devoted a great deal of attention to
attacking China, in opposition to Canadians' desire that Canada be a
zone for peace.

(To
access articles individually click on the black headline.) PDF
PREVIOUS
ISSUES | HOME
Website: www.cpcml.ca
Email: editor@cpcml.ca | 
